QUAXAR
Project Description
Enhanced the ASM UX to increase efficiency within the CTI Platform
Project Type
Website
Deliverable
Wireframe, User Guide

Goal
The goal is to improve the information architecture and user flow of the ASM (Attack Surface Management) service so that security teams can detect externally exposed assets in real time, quickly identify vulnerabilities, and proactively respond to potential threats.
Challenge
Due to the dynamic creation and changes of various exposed assets (domains, IPs, cloud resources, etc.), the previous ASM screens often missed asset detection and critical details, resulting in inefficient analysis and response.
Outcome
The final deliverable proposed a solution that enhances asset detection accuracy and risk visibility, so that security teams can swiftly detect and respond to hidden threats and efficiently search for specific assets using various search options.
4
Weekly Meetings
127
Document Pages
2
Deliverables
Project timeline
Discover
VoC Analysis
Used an affinity diagram method with S2W internal stakeholders to clarify the goals we needed to solve. We collected a wide range of ideas from different perspectives, grouped them by similar themes, and reorganized them to derive meaningful insights and define clear problem-solving directions.
Define
Aligning Direction
Defined a clear goal to provide an asset-centric view of security information, measurable KPIs, and potential risks to service effectiveness, then confirmed the direction through stakeholder voting.
Define
Stakeholder Interview
In this phase, we conducted stakeholder interviews to identify critical pain points and align everyone’s expectations. This process helped turn vague concerns into clear, actionable design requirements. As a result, the team could prioritize what problems to solve first and ensure that our solutions would effectively meet real user needs.
Develop
UX/UI Concept
This UX/UI concept empowers security teams with an AI assistant for smarter workflows, personalized threat intelligence for each organization, and seamless reporting features that turn complex data into clear, shareable insights.
Develop
Search Policy
We documented the organization’s search operator policies in a clear manual to standardize how different teams use advanced search queries. This ensures that security analysts can accurately search and filter large asset and threat datasets, while maintaining consistent and reliable search results across the system.
Develop
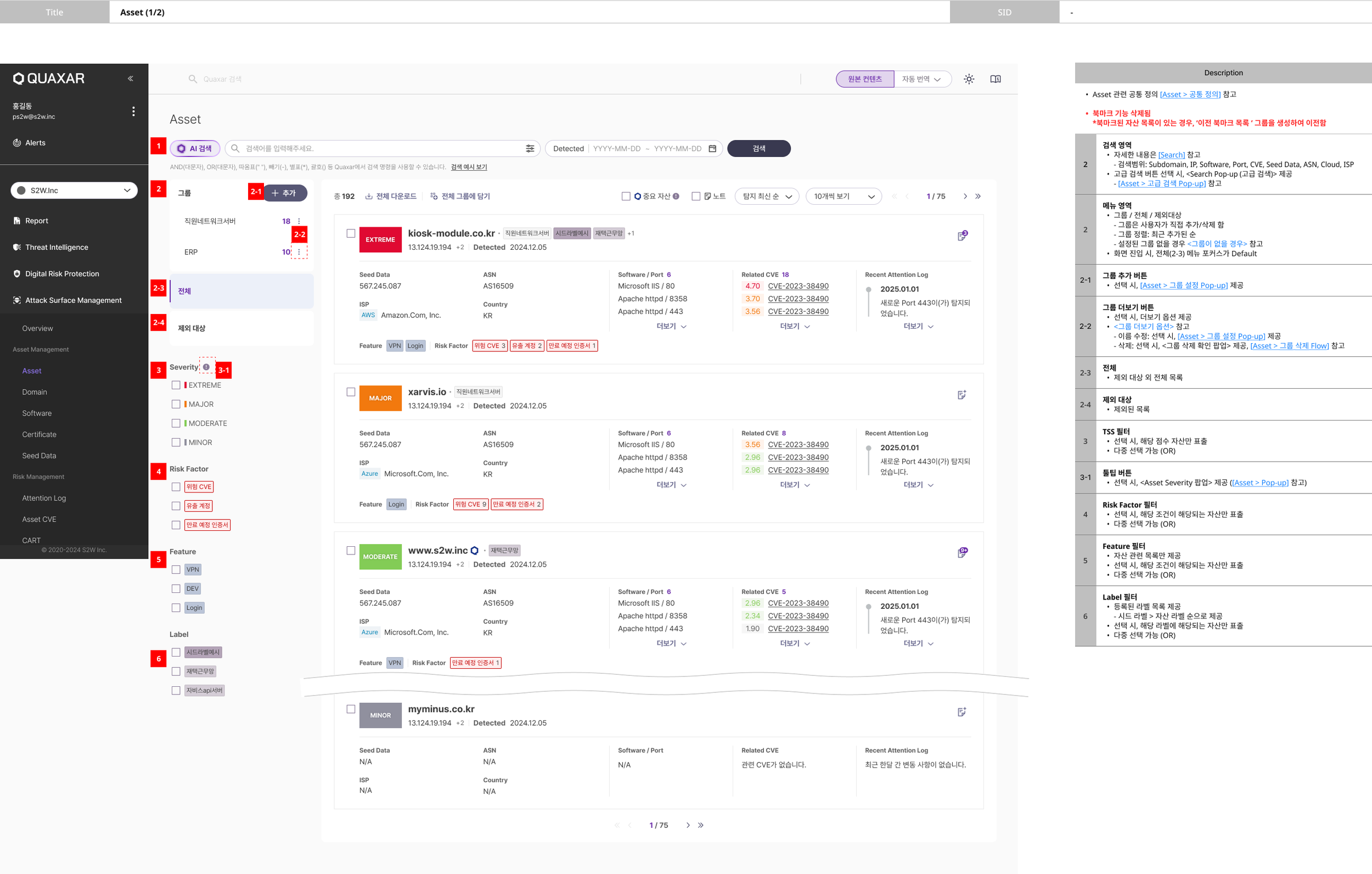
Wireframe
In this phase, We revised the wireframe design focusing on the ASM menu structure to help users more intuitively discover and manage externally exposed assets. I reorganized the information architecture and refined key user flows to match real-world scenarios, ensuring that security teams can navigate and act on critical asset data more efficiently.
Develop
Wireflow
Conversation logic was designed to enable the chatbot to accurately understand context and respond appropriately based on different dialogue scenarios. This approach aims to support a natural and consistent conversational experience for users while establishing a flexible structure that can adapt to various learning situations.